Aobo Keylogger is a small utility that can record the keystrokes captured by any Mac computer and send the logs by email or upload them to a FTP server. Moreover, Aobo Keylogger can document visited websites, chat conversations, and capture desktop screenshots. Record keystroke Keystroke recorder Keystroke logger Keylogger Log. AOBO KEYLOGGER FOR MAC 2016: New – Remote installation keylogger for Mac. Real-time monitoring, keystroke logging with screenshot capture, social network and application activity capture. Install remotely, perfect for monitoring your child’s activity and ensuring their safety. One of the only remote installation applications for Mac available. Aobo Keylogger free download - Revealer Keylogger Free, All In One Keylogger, Elite Keylogger, and many more programs. Aobo Keylogger Professional for Mac: Free Download - Invisible keylogger with email, FTP, and password support. Download the latest versions of the best Mac apps. Try Aobo Keylogger standart + Get 10% Off Buy Aobo Keylogger Pro With 10% Off Coupon Aobo Keylogger is one the best mac logging applications. Aobo Keylogger for Mac Standard, the invisible keylogger for Mac OS X with multiple-user support, has the ability to monitor all the activities on the targeted Mac, including keystrokes typed, IM chatting conversations entered, comments posted on social media, websites visited and so on.
Aobo Keylogger Download
If you are a parent, you need to know what your kids are doing with your computer. You don’t want them to spend too much time chatting with some unknown people on social media. You also don’t want them to spend most of their time playing games. If you give them a computer, you want them to use it to do their homework and learn some useful things. It’s the same with your employees. You don’t want them to waste their time in the office playing games and watching videos. You want them to work. This is where keystroke logger software is becoming necessary, as it helps to monitor your computers and see what your kids or employees are doing with it.
Related:
SoftActivity Keylogger
SoftActivity Keylogger is a home computer monitoring software designed specifically for parents who want to monitor what their kids are doing with their computers. This software allows you to log every user action, log email sent and received, record IM chat, view typed keystrokes, and capture screenshots for every action. It is available for Windows devices.
Keylogger Platinum
Keylogger Platinum is a hidden keyboard monitoring software that allows you to stealthily monitor the keystrokes of your computer. This Windows software helps you to protect your children online, save relations, improve your business productivity, and recover lost text. This software is completely free.
Elite Keyloggers
Elite Keyloggers is a keystroke logger software that is completely invisible and undetectable. It is available for Windows and Mac platforms. With this software, you can monitor clipboard and application, intercept URL, record chats and emails, record keystrokes, and collect passwords.
BlackBox Security Monitor
BlackBox Security Monitor allows you to monitor your computer and internet usage with privacy and efficiency. You can use this software to use mobile devices for monitoring. It provides an add-on that allows you to monitor hundreds of computers at the same time. This software is available for Windows desktop and server.
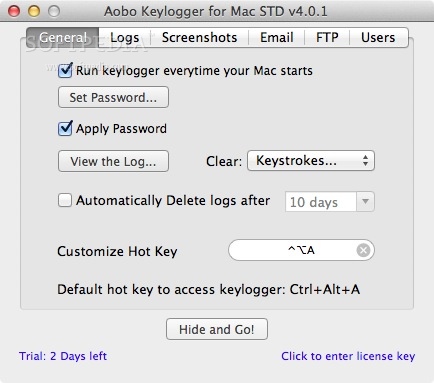
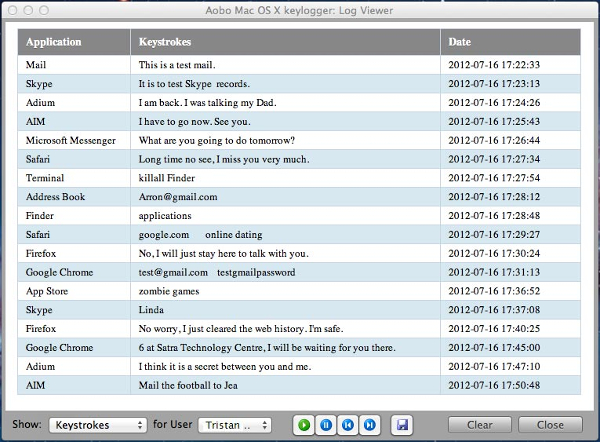
Aobo Keylogger
Aobo Keylogger is a keylogging software that you can install on your Mac computer, which can be used at home or business. It features monitoring for social activities, passwords, instant messages, websites visited, chat logs, IP address, and website history.
Best Free Keylogger
Best Free Keylogger is a keylogger software for Windows, which allows you to monitor the computer usage of your children or employees. It features keystroke recording, internet activity recording, chat and password logging, clipboard monitoring, application monitoring, invisible mode, and password protection.
Revealer Keylogger
Revealer Keylogger is a computer monitoring software that provides conversation monitoring, remote monitoring, and invisible mode. It features password protection, keystroke recorder, and screen capture. This software is available for Windows.
Keylogger
Keylogger is a keylogger software that provides the monitoring system for all of your computer activities. It features keystroke recording, screenshot capturing, clipboard monitoring, application activity monitoring, employee monitoring, and Skype recording. This software is available for Windows and Mac.
Other Keystroke Logger Software for Different Platforms
You can use keystroke logger software for Windows, Mac, and other platforms. This software allows you to monitor both computers and mobile devices.
Actual Keylogger
Actual Keylogger is a keylogger software for Windows that allows you to monitor your computer activities when you are not present. This software offers various unique features, including case-sensitive keystroke recorder, limit setting on clipboard content, flexible configuration system, and hidden mode. It is ideal for parents, CEOs, admins, and teachers.
Kidlogger
Kidlogger is a keylogger software that is designed to help parents who want to monitor their kids’ activities online. It features web history monitoring, record keystrokes, time tracking, screenshots, USB and CD usage, and used files and folders. This software is available for Android, Windows, and Mac.
AMac Keylogger
AMac Keylogger is a powerful and reliable keylogger software for Mac OS X. This app can be used for family, business, parents, and regular Mac users. It offers various features, including undetectable monitoring, keystroke and password recording, website activity recording, IM chat activity recording, and desktop screenshot capture.
Logkeys
Logkeys is a good keylogging software for Ubuntu, providing simple yet powerful keylogging functionalities that won’t crash your system. It can be used to record all the keystrokes that are typed on your Ubuntu system. It is an open source software that is updated regularly.
All in One Keylogger – Best Keystroke Logger Software of 2016
All in One Keylogger is a computer surveillance software that helps you to log all activities on your computer. The encrypted log delivery allows you to keep the software undetected and invisible. It features key logging, clipboard logging, internet logging, microphone logging, printer logging, and user inactivity logging. This software is available for all versions of Windows.
What is Keystroke Logging Software?
Keystroke logging software is a type of software that allows you to record keystrokes and other activities on your computers. It is the software that is usually used by parents and business owners to monitor user activity on their computers. Parents want to make sure that their kids use the computer to study, not to play games too much.
Business owners also want to make sure that their computers are used to work, not to watch videos and chat on social media websites. The installation of this software is usually hidden and undetected so that the trace of the software is not visible on the target computer.
How to Install Keystroke Logging Software?
To install a keystroke logging software, you simply need to download the installation file from the official website of the respective software and run the installation file on the target computers. These target computers are the computers that you want to monitor. The installation of the software is usually done quickly and stealthily, meaning that you cannot see any installation folder of this software on your system.
The next step is just to wait for the software to send you regular log files that report the user activity on the target computer.
Keystroke logger software is an important software for parents and business owners to monitor the activity on their computers, to ensure that the computers are used properly. This software can also help you to protect the security and privacy of your children and business since you will know everything that your children and employees are doing on your computer.
You can protect your children from chatting with unknown people online, and you can also spot a bad employee who is trying to leak secret company information immediately.
Related Posts
What is AoBo?
AoBo (also known as OSX/ABK) is a keystroke logger, which can be purchased from a company called AoBo software. It is advertised as allowing people to monitor children and employees, however, research shows that AoBo opens shared AirPort access, records keystrokes and passwords and sends logs to a remote server.
If distributed by cyber criminals, this keylogger can be misused for malicious purposes.
Keystroke loggers record keyboard input. I.e., they record data entered with the keyboard. Note that even legitimate keyloggers can be used for malicious purposes. Generally, cyber criminals use software of this type to steal sensitive information. For example, entered credit card details and login credentials (usernames/email addresses, passwords).
This information can be misused to steal identities, personal accounts (social media, email), and to make fraudulent transactions and purchases, etc. Additionally, AoBo can be used to open a shared AirPort access. Therefore, cyber criminals can connect to the stations that share the same network name, encryption setup and password.
Therefore, users tricked to install AoBo could become victims of identity theft, lose access to various accounts (depending on stolen login credentials), suffer monetary loss, have problems relating to online privacy, browsing safety, etc. If this software was not installed on your system intentionally, remove it immediately.
Since this keylogger sends recorded data to a remote server, it should never be trusted.
| Name | OSX/ABK keystroke logger |
| Threat Type | Keystroke logger. |
| Detection Names | Avast (MacOS:AoboKeylogger-H [PUP]), BitDefender (Application.MAC.OSX.AoboKeylogger.A), ESET-NOD32 (A Variant Of OSX/KeyLogger.AoboKeylogger.E), Kaspersky (Not-a-virus:Monitor.OSX.Keylogger.o), Full List (VirusTotal). |
| Symptoms | When distributed by cyber criminals, keystroke loggers stealthily infiltrate the victim's computer and remain silent, and thus no particular symptoms are clearly visible on an infected machine. |
| Distribution methods | Infected email attachments, malicious online advertisements, social engineering, software 'cracks'. |
| Damage | Stolen passwords, banking information, identity theft. |
| Malware Removal (Mac) | To eliminate possible malware infections, scan your Mac with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. |
In summary, keyloggers are used for both legitimate and malicious purposes. They are used to monitor users' computing activity by tracking keyboard input. When people install this software inadvertently, they may be unaware for an indefinite period of time.
Common methods employed by cyber criminals to trick users into installing keyloggers and various other malicious programs are described in the next paragraph.
How did malware install on my computer?
One of the most common ways to spread malicious programs is through emails (malspam campaigns). In such cases, cyber criminals send malicious files or website links designed to download them, and encourage recipients into executing the malicious file.
Typically, they attach Microsoft Office documents, PDF documents, executable files such as .exe, archive files (ZIP, RAR) or JavaScript files. Malware is also distributed by tricking users installing Trojans, some of which cause chain infections by installing other malicious software.
Fake software updating tools can infect systems by installing malware instead updating installed software, or by exploiting bugs/flaws of outdated programs. Untrusted software download sources such as freeware download websites, free file hosting websites, Peer-to-Peer networks (torrents, eMule), and various third party downloaders, are also used to distribute malware.
People infect their computers when they download and open the malicious files, which are often disguised as legitimate and regular. Malware is also spread through software 'cracking' (unofficial activation) tools. These programs supposedly activate licensed software (illegally), however, they often install malware instead.
How to avoid installation of malware
Software and files should be downloaded from official pages and via direct download links. Study all emails that contain files and/or website links before opening them, especially when the emails are sent from unknown, suspicious addresses. Installed programs must updated and activated with tools/implemented functions) provided by the official developers.
Note that it is illegal to use unofficial ('cracking') tools to activate any licensed software. Regularly scan your computer with reputable antivirus or anti-spyware software, which should be kept up to date. If your computer is already infected with PUAs, we recommend running a scan with Combo Cleaner Antivirus for macOS to automatically eliminate them.
Instant automatic Mac malware removal:Manual threat removal might be a lengthy and complicated process that requires advanced computer skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of Mac malware. Download it by clicking the button below:
▼ DOWNLOAD Combo Cleaner for MacBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. Limited three days free trial available.
Quick menu:
- STEP 1. Remove PUA related files and folders from OSX.
- STEP 2. Remove rogue extensions from Safari.
- STEP 3. Remove rogue add-ons from Google Chrome.
- STEP 4. Remove potentially unwanted plug-ins from Mozilla Firefox.
Video showing how to remove adware and browser hijackers from a Mac computer:
Potentially unwanted applications removal:
Remove potentially unwanted applications from your 'Applications' folder:
Click the Finder icon. In the Finder window, select 'Applications'. In the applications folder, look for 'MPlayerX', 'NicePlayer', or other suspicious applications and drag them to the Trash. After removing the potentially unwanted application(s) that cause online ads, scan your Mac for any remaining unwanted components.
Combo Cleaner checks if your computer is infected with malware. To use full-featured product, you have to purchase a license for Combo Cleaner. Limited three days free trial available.
Remove osx/abk keystroke logger related files and folders:
Click the Finder icon, from the menu bar. Choose Go, and click Go to Folder...
Check for adware-generated files in the /Library/LaunchAgents folder:
In the Go to Folder... bar, type: /Library/LaunchAgents
In the “LaunchAgents” folder, look for any recently-added suspicious files and move them to the Trash. Examples of files generated by adware - “installmac.AppRemoval.plist”, “myppes.download.plist”, “mykotlerino.ltvbit.plist”, “kuklorest.update.plist”, etc. Adware commonly installs several files with the same string.
Check for adware generated files in the /Library/Application Support folder:
In the Go to Folder... bar, type: /Library/Application Support
In the “Application Support” folder, look for any recently-added suspicious folders. For example, “MplayerX” or “NicePlayer”, and move these folders to the Trash.
Check for adware-generated files in the ~/Library/LaunchAgents folder:
In the Go to Folder bar, type: ~/Library/LaunchAgents
In the “LaunchAgents” folder, look for any recently-added suspicious files and move them to the Trash. Examples of files generated by adware - “installmac.AppRemoval.plist”, “myppes.download.plist”, “mykotlerino.ltvbit.plist”, “kuklorest.update.plist”, etc. Adware commonly installs several files with the same string.
Check for adware-generated files in the /Library/LaunchDaemons folder:
In the Go to Folder... bar, type: /Library/LaunchDaemons
In the “LaunchDaemons” folder, look for recently-added suspicious files. For example “com.aoudad.net-preferences.plist”, “com.myppes.net-preferences.plist”, 'com.kuklorest.net-preferences.plist”, “com.avickUpd.plist”, etc., and move them to the Trash.
Scan your Mac with Combo Cleaner:
If you have followed all the steps in the correct order you Mac should be clean of infections. To be sure your system is not infected run a scan with Combo Cleaner Antivirus. Download it HERE. After downloading the file double click combocleaner.dmg installer, in the opened window drag and drop Combo Cleaner icon on top of the Applications icon. Now open your launchpad and click on the Combo Cleaner icon. Wait until Combo Cleaner updates it's virus definition database and click 'Start Combo Scan' button.
Combo Cleaner will scan your Mac for malware infections. If the antivirus scan displays 'no threats found' - this means that you can continue with the removal guide, otherwise it's recommended to remove any found infections before continuing.
After removing files and folders generated by the adware, continue to remove rogue extensions from your Internet browsers.
OSX/ABK keystroke logger removal from Internet browsers:
Remove malicious extensions from Safari:
Remove osx/abk keystroke logger related Safari extensions:
Open Safari browser, from the menu bar, select 'Safari' and click 'Preferences...'.
In the preferences window, select 'Extensions' and look for any recently-installed suspicious extensions. When located, click the 'Uninstall' button next to it/them. Note that you can safely uninstall all extensions from your Safari browser - none are crucial for normal browser operation.
- If you continue to have problems with browser redirects and unwanted advertisements - Reset Safari.
Remove malicious plug-ins from Mozilla Firefox:
Remove osx/abk keystroke logger related Mozilla Firefox add-ons:
Open your Mozilla Firefox browser. At the top right corner of the screen, click the 'Open Menu' (three horizontal lines) button. From the opened menu, choose 'Add-ons'.
Choose the 'Extensions' tab and look for any recently-installed suspicious add-ons. When located, click the 'Remove' button next to it/them. Note that you can safely uninstall all extensions from your Mozilla Firefox browser - none are crucial for normal browser operation.
- If you continue to have problems with browser redirects and unwanted advertisements - Reset Mozilla Firefox.
Remove malicious extensions from Google Chrome:
Aobo Keylogger Serial
Remove osx/abk keystroke logger related Google Chrome add-ons:
Open Google Chrome and click the 'Chrome menu' (three horizontal lines) button located in the top-right corner of the browser window. From the drop-down menu, choose 'More Tools' and select 'Extensions'.
In the 'Extensions' window, look for any recently-installed suspicious add-ons. When located, click the 'Trash' button next to it/them. Note that you can safely uninstall all extensions from your Google Chrome browser - none are crucial for normal browser operation.
- If you continue to have problems with browser redirects and unwanted advertisements - Reset Google Chrome.